Blog
Subscribe to our blog

Which Do I Need, a Gateway or a Service Mesh?
This is the first in a series of articles on Tetrate Enterprise Gateway for Envoy (TEG), the enterprise-ready distribution of Envoy Gateway, the cloud-native service gateway. Get access to TEG…
Read More arrow_forward
Authservice: the Future of Cloud-Native Authentication and Compliance
In the rapidly evolving landscape of cloud-native technologies, the introduction of Authservice marks a pivotal moment. This groundbreaking open-source project by Tetrate in conjunction with the United States Air Force’s…
Read More arrow_forward
Application High Availability Architecture with Tetrate’s Enterprise Service Mesh
Modern multi-service, multi-cloud applications can be fragile, particularly when running in highly-automated infrastructure with many moving parts. To make them robust in the face of production traffic, you need to…
Read More arrow_forward
Announcing Tetrate Enterprise Gateway for Envoy 1.0
We are thrilled to announce the general availability of Tetrate Enterprise Gateway for Envoy (TEG), the only 100% upstream, enterprise-ready distribution of Envoy Gateway. Envoy Gateway is the cloud-native service…
Read More arrow_forward
4 Envoy Extensibility Mechanisms: How to Boost Envoy Gateway Performance and Functionality
This is the second in a series of articles on the value of Envoy Gateway as it reaches the 1.0 release milestone and ready for production use. Envoy Gateway has reached 1.0…
Read More arrow_forward
KubeCon EU 2024: Tetrate’s Insights and Highlights from Paris
Last month’s KubeCon EU 2024 in Paris was a landmark event for the cloud native community, drawing an impressive crowd of 12,000 attendees from across the globe. Tetrate, as a…
Read More arrow_forward
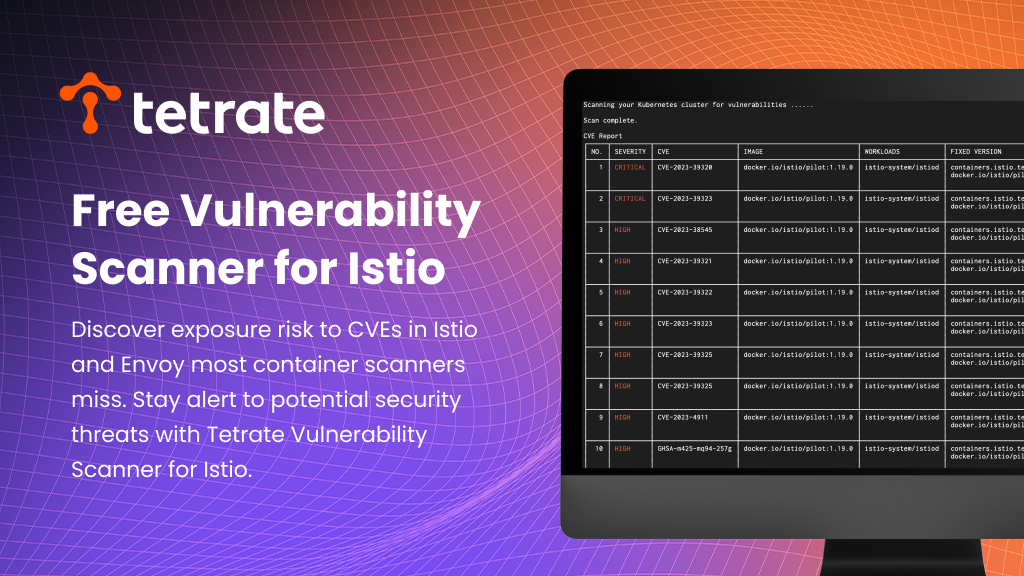
TVS: Istio and Envoy CVE Scanning Solution
This article will introduce Tetrate’s newly launched tool – Tetrate Vulnerability Scanner (TVS), a CVE scanner customized for Istio and Envoy. Before diving into the specific features of TVS, let’s…
Read More arrow_forward
Building Client-Side Availability and Resiliency with a Service Mesh and Envoy Gateway
How to Think about Availability and Resiliency in Client Applications This is the first in a series of articles on the value of Envoy Gateway as it reaches the 1.0…
Read More arrow_forward
Announcing Envoy Gateway 1.0
Envoy Gateway Reaches 1.0 We are thrilled to announce that Envoy Gateway has reached 1.0. Tetrate is proud to have helped lead the development of the Envoy Gateway project in…
Read More arrow_forward